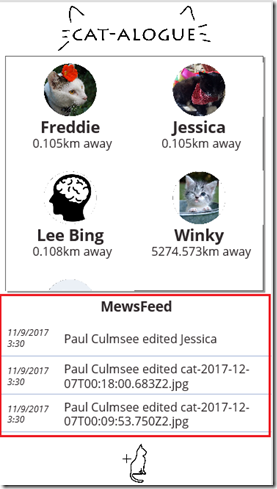
Some seriously powerful (and free) PDF functionality in PowerApps and Flow
Hiya Pretty much every time I run a project kick-off meeting involving tools like SharePoint or PowerApps, I always ask the group the following question: “If you had <insert goal here>, how would things be different to now”? (Replace <insert …
Some seriously powerful (and free) PDF functionality in PowerApps and Flow Read more »