WIFI Security: Background, Risks and Mitigation Part 2
Like my posts on IT governance standards, I produced this training material some time back when I was doing a lot of IT security work. I’ve since moved onto other IT disciplines, but I hope that this article is of some use to those looking for an introduction to WIFI security. I have divided the material into two parts. The first half is background and theory, and this post illustrates a practical example.
First up, let’s finish off a little theory to go with the first post.
Other WIFI Security Measures
WEP and the much improved WPA should not be considered alone. Security in general requires a holistic approach to determine what functionality the business requires, what techniques can be used to provide that functionality and then assurance of the security of those features. Below are two additional techniques regularly used in conjunction with WEP or WPA to improve the security of a WLAN.
MAC Address Filtering
A common feature available with wireless access devices is the means to restrict access to only wireless devices that have their network (MAC) address configured in a filter list. Therefore, any device that tries to authenticate with a MAC address not matching the list will be rejected.
This method is not foolproof. If traffic can be decrypted then a valid MAC address could be determined and used to access the network.
Separate VLAN/DMZ for Wireless LAN
Most medium to large networks utilise virtual LAN’s (VLAN’s) to separate IP networks into logical groupings for security, performance and management reasons. Most good quality layer 3 switches provide VLAN’s that allow you to define firewall rules or access lists to restrict what resources on the network that wireless networks clients can access.
For more protection, the wireless network can be placed behind a fully featured stateful firewall rather than a VLAN alone.
WPA Wireless Clients Sample Implementation
This section shows an example of implementing WPA Enterprise with PEAP. Three components are required.
- The supplicant (the WIFI client),
- The Authenticator (the Access Point) and;
- An Authentication Server (A Radius server such as Microsoft IAS Server).
In this example the Access Point is a Cisco Aironet 1310 Series Outdoor Access Point/Bridge1 running IOS 12.3(7)JA.
In addition, since we are using PEAP, we need a suitable certificate server and we have used Microsoft Certificate Services.
Since we are using Microsoft IAS for Radius, which integrates with Active Directory, we have created 2 new Active Directory groups called "Wireless Users" and "Wireless Computers" respectively. These groups will be used to determine what computers and users are allowed access to the WIFI network. This ensures a high level of granularity for IT staff to manage access.
Configuring IAS (RADIUS)
IAS is a free component that is supplied with Win2k/Win2003 but is not installed by default. It can be installed via the Control Panel->Add/Remove Programs/Windows Components applet.
Both IAS and the authenticating access point need to be configured to perform Radius authentication. Firstly, you need to register IAS in Active Directory, so that IAS policies can be used on Active Directory users and computers to govern access.
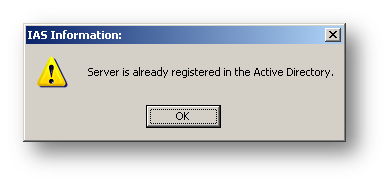
In the left hand pane of the IAS management console, select Internet Authentication Service (Local) and right click to select the Register Server in Active Directory option.
If the server is already registered in active directory, this message will be shown
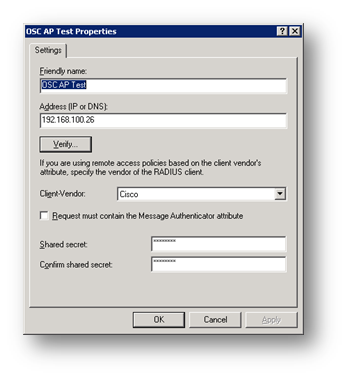
Adding the Access Point as a Radius Client
In IAS, you create a new RADIUS client and enter a shared secret.
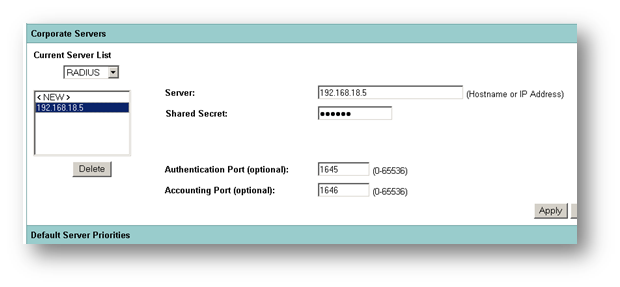
Adding the IAS Server as a Radius Server on the Access Point
On the access point, the detail of the IAS server is entered.
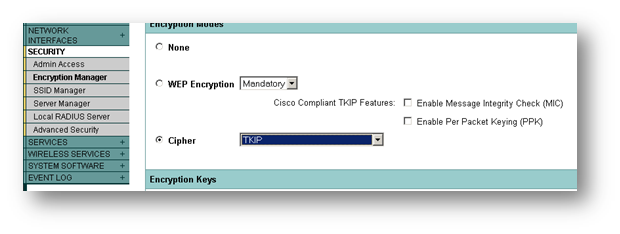
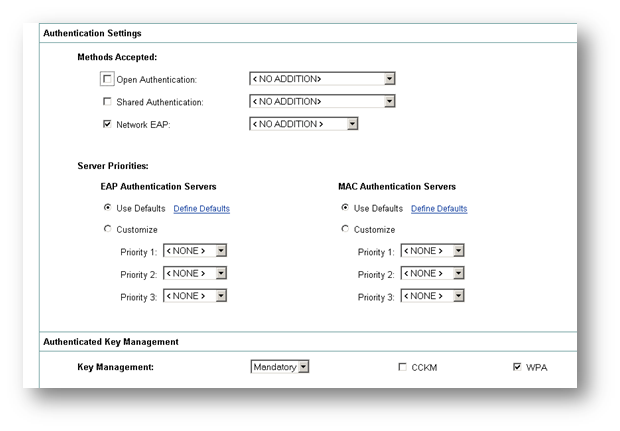
Next we need to configure the Access Point to accept WPA clients and authenticate them to Radius. To do this, we first set encryption to WPA/TKIP.
Next we set the SSID to use Open Authentication and Network/EAP authentication. Network EAP is the better of the two, but Cisco have noted that ‘Some non-Cisco Aironet client adapters do not perform 802.1x authentication to the access point/bridge unless you configure Open authentication with EAP.’
We have already configured the RADIUS server, so we just use the default list. Under Key Management, we set it to mandatory and choose WPA. Accounting can also be enabled, and log on and log off events will be sent to the RADIUS server.
Configuring a Digital Certificate for the IAS Server.
If the server running IAS is already part of Active Directory, and there is a Certificate Server on the Active Directory Domain, the IAS server will already have a computer certificate installed. This can be verified using the Certificate Services MMC Span-In.
Open the Local Computer certificate store, choose Personal/Certificates and you should find a certificate matching the name of this computer. For example:
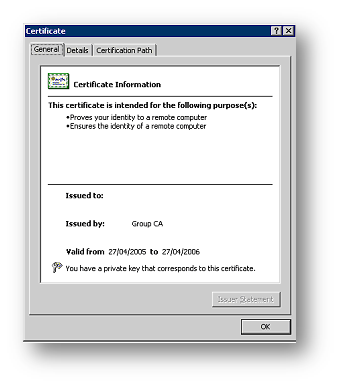
If you do not have a computer certificate, you need to obtain one via a certificate authority. This is not covered in this document.
Configuring IAS Wireless Policy
At this point we now need to configure the policy on the Radius server so that when a wireless device connects, the conditions that allow it to join the network are defined. The policies set will be to ensure the computer and user id supplied are members of the "Wireless Users" and "Wireless Computers" active directory groups.
User Access
The first policy to be created is for the user accounts that will be connecting to the wireless network. The wireless connection type will be defined and then the appropriate active directory security group will be specified.
In IAS Management console, create a new Remote Access Policy, select "Set up a custom policy" and enter "WFIC Wireless User Access" as the Policy name.
Now we add the conditions required for this remote access policy
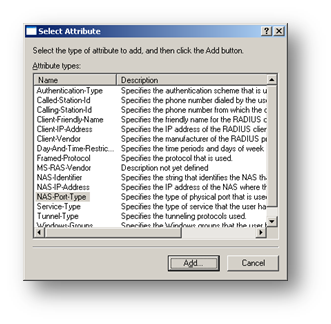
Select Client-IP-Address, Add the IP address of the Wireless Access Point and click Ok
Select Windows-Groups and then click Add. Enter the wireless user groups "Wireless Users" and "Wireless Computers" as described earlier and click OK
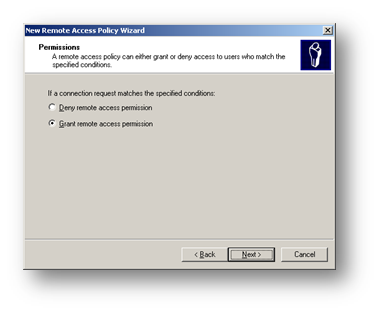
Now we have completed the conditions for using this wireless policy. Click Next and grant remote access permission.
Now we have to specify the PEAP settings. Click Profile
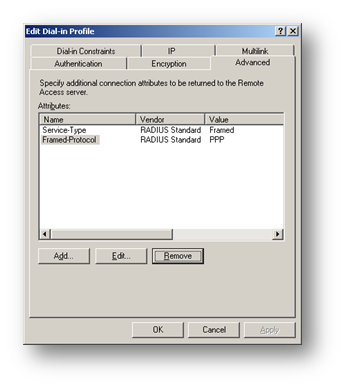
Select the Advanced tab, highlight the Framed-Protocol (RADIUS Standard PPP) attribute and click Remove
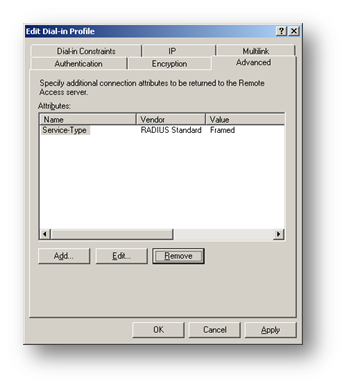
Select the Encryption tab
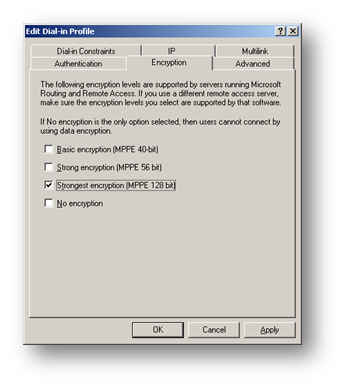
Select the Encryption tab and remove all tick boxes, leaving only the Strongest Encryption (MPPE 128-bit) option ticked
Select the Authentication tab
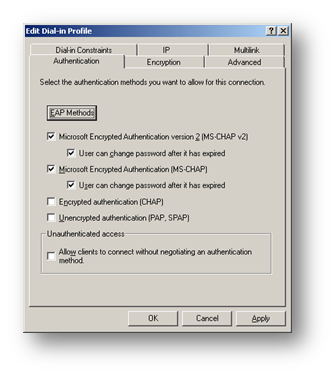
Select the Authentication tab and click EAP Methods
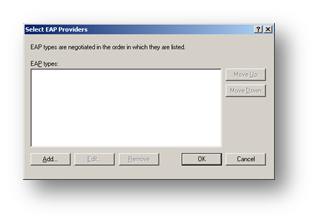
Click Add to add an EAP type
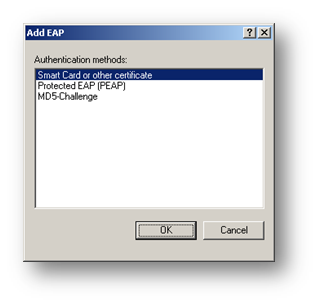
Select PEAP and click OK. Now Click Edit to modify the PEAP type

Ensure that the certificate is the correct and ensure that MSCHAP is set as the EAP type
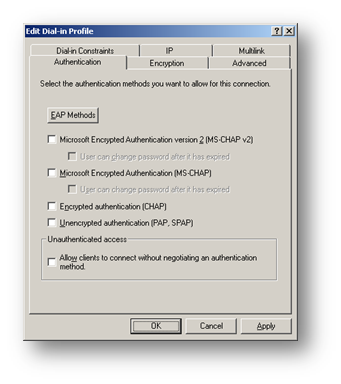
Back on the Authentication tab remove all other tick box options then click OK
You may see a message asking if you would like to view the online help to follow and configure dial-in settings
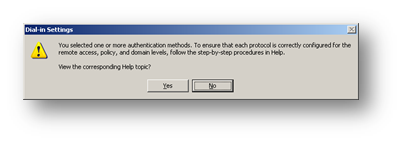
Click No and Next to continue. The wizard will now tell you the profile is complete and summarise the conditions and profile settings.
Computer Policy
Another policy can optionally be created for Domain Computers. The policy steps are identical to the steps outlined in the user policy except during the setting of policy conditions, you use the Active Directory group that the wireless computers are a member of.
Granting Active Directory Rights
The last step is to ensure that the user and computer accounts in Active Directory have rights to ‘dial in’ – which is Microsoft’s term for using Radius Authentication.
A user account needs "Control Access through Remote Access Policy" set.
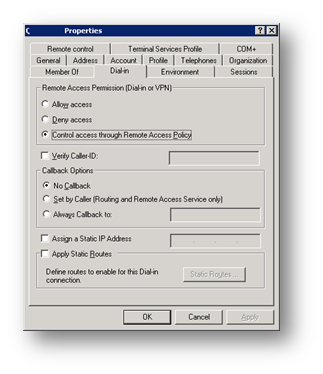
A computer account needs the same setting.
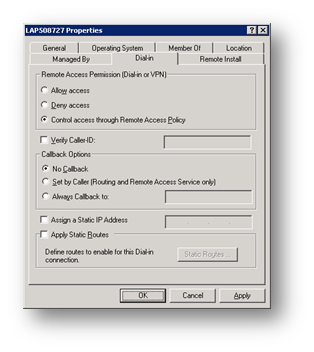
Wireless Client Configuration Settings
This section only deals with the configuration of Windows XP Clients
Digital Certificate
Using PEAP, the WIFI clients do not need to use a digital certificate. Only the server uses one to identify itself to the client. However, the clients need to trust the certificate authority (CA) that issued the server certificate. To do this, the certificate of the CA needs to be added to the trusted certificate list on the client.
If the computer is a member of the Active Directory Domain, the CA certificate is likely already installed. This can be checked using the same steps defined in the section "Configuring a Digital Certificate for the IAS Server" except you go to the "Trusted Root Certification Authorities" store to find the CA certificate.
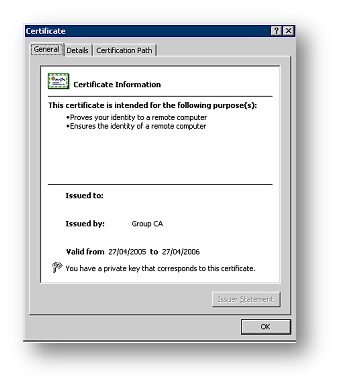
If the certificate is not installed and if the CA certificate Using Microsoft Certificate Services, it is easy to obtain and install it. The certificate can be installed by double clicking on the certificate file stored on a shared folder, floppy or USB device. Alternatively, the client can request the CA certificate from the CA website.
Wireless Networking Configuration
In the properties of the wireless network adapter, add a new wireless network, specifying WPA and TKIP
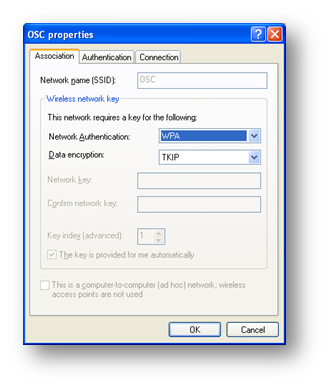
On the authentication tab, choose PEAP as the EAP type
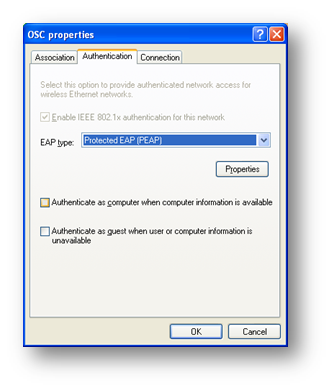
Click Properties and tick ‘validate server certificate’ and ensure the CA that issued the server certificate is selected.
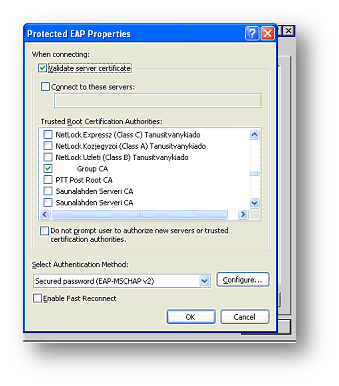
If the certificate authority is not listed above, than this machine does not trust it and it needs to be added to the trust list as per section titled "Digital Certificate"
Ensure ERP-MSCHAPv2 is selected at the ‘select authentication method’ list and click ‘properties’.
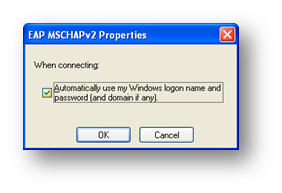
This dialog box allows you to select if XP will attempt user authentication based on the currently logged in user, or prompt for credentials to be entered. If this workstation is a member of the domain, and the user logs into it via a domain account, this should be ticked.
Click OK and OK again to return to the Wireless network properties screen.
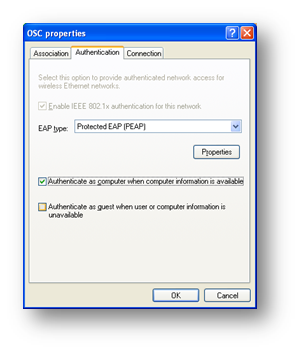
If a computer authentication policy has been chosen as per section entitled "Computer Policy", tick the "Authenticate as computer when computer information is available".
At this point the wireless client should be able to connect to the wireless network if the user and computer credentials are valid. The event logs on the IAS server now will show detailed records of all wireless network authentication attempts including username, date/time, IAS policy used and whether access was granted or denied.
Below is a sample IAS log entry from an access point using the IP address 192.168.100.26 and an IAS policy called "AP Test".
Event Type: Information
Event Source: IAS
Event Category: None
Event ID: 1
Date: 20/01/2006
Time: 4:45:07 PM
User: N/A
Computer: MYSERVER
Description:
User DOMAIN\some guy was granted access.
Fully-Qualified-User-Name = domain.net/MY Company/DOMAIN/Some Guy
NAS-IP-Address = 192.168.100.26
NAS-Identifier = bridge
Client-Friendly-Name = AP Test
Client-IP-Address = 192.168.100.26
Calling-Station-Identifier = 0013.ff10.427c
NAS-Port-Type = Wireless – IEEE 802.11
NAS-Port = 282
Proxy-Policy-Name = Default Connection
Authentication-Provider = Windows
Authentication-Server = <undetermined>
Policy-Name = Test – Wireless
Authentication-Type = PEAP
EAP-Type = Secured password (EAP-MSCHAP v2)
Leave a Reply