IT Governance Standards: COBIT, ISO17799/27001, ITIL and PMBOK – Part 4
The content of this blog is essentially material I compiled for training sessions that I ran last year. It was originally PowerPoint, but I hope that this blog version is useful. Some of the legislative stuff is probably now out of date, and it was for an Australian audience – moral of the story is to do your own research.
For part 1 of this presentation, view this post, part 2 this post and part 3 here.
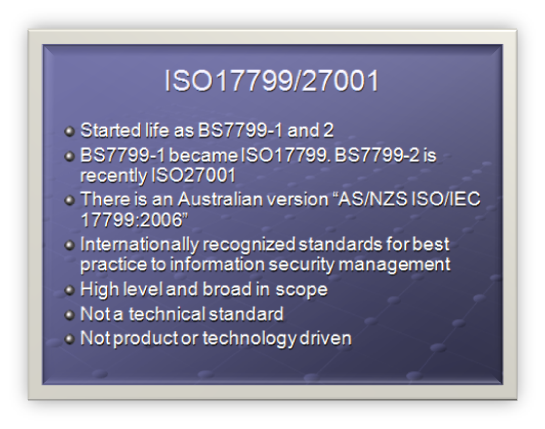
ISO17799/27001
- Started life as BS7799-1 and 2
- BS7799-1 became ISO17799. BS7799-2 is recently ISO27001
- There is an Australian version "AS/NZS ISO/IEC 17799:2006"
- Internationally recognized standards for best practice to information security management
- High level and broad in scope
- Not a technical standard
- Not product or technology driven
ISO 17799 is a direct descendant of part of the British Standard Institute (BSI) Information Security Management standard BS 7799. The BSI (www.bsi-global.com) has long been proactive in the evolving arena of Information Security.
The BS 7799 standard consists of:
- Part 1: Information Technology-Code of practice for information security management
- Part 2: Information security management systems-Specification with guidance for use.
BS7799 was revised several times, and by 2000 information security had become headline news and a concern to computer users worldwide. Demand grew for an internationally recognized information security standard under the aegis of an internationally recognized body, such as the ISO. This demand led to the "fast tracking" of BS 7799 Part 1 by the BSI, culminating in its first release by ISO as ISO/IEC 17799:2000 in December 2000.
In 2006, adoption of BS 7799 Part 2 for ISO standardization was completed and now forms ISO27001.

ISO17799 vs. ISO27001
- ISO17799 is a code of practice – like COBIT it deals with ‘what’, not ‘how’.
- ISO27001 This is the ‘specification’ for an Information Security Management System (ISMS). It is the means to measure, monitor and control security management from a top down perspective. It essentially explains how to apply ISO 17799 and it is this part that can currently be certified against
Unlike COBIT, ISO17799 does not include any maturity model sections for evaluation. (incidentally, nor does ISO9000)
ISO 17799 is a code of practice for information security. It details hundreds of specific controls which may be applied to secure information and related assets. It comprises 115 pages organized over 15 major sections.
ISO 27001 is a specification for an Information Security Management System, sometimes abbreviated to ISMS. It is the foundation for third party audit and certification. It is quite small because it doesn’t actually list the controls, but more a methodology for auditing and measuring. It comprises 34 pages over 8 major sections.
ISO17799 is:
- an implementation guide based on suggestions.
- used as a means to evaluate and build a sound and comprehensive information security program.
- a list of controls an organization "should" consider.
ISO27001 is:
- an auditing guide based on requirements.
- used as a means to audit an organizations information security management system.
- a list of controls an organization "shall" address.
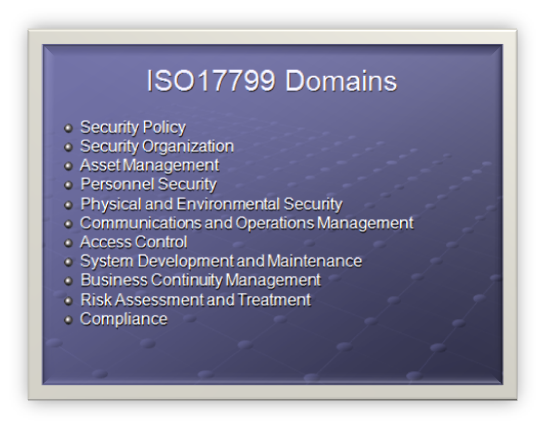
ISO17799 Domains
- Security Policy
- Security Organization
- Asset Management
- Personnel Security
- Physical and Environmental Security
- Communications and Operations Management
- Access Control
- System Development and Maintenance
- Business Continuity Management
- Risk Assessment and Treatment
- Compliance
ISO17799 divides up security into 12 domains.
Within each domain, information security control objectives (if you recall that is he same terminology as COBIT) are specified and a range of controls are outlined that are generally regarded as best practice means of achieving those objectives.
For each of the controls, implementation guidance is provided.
Specific controls are not mandated since each organization is expected to undertake a structured information security risk assessment process to determine its requirements before selecting controls that are appropriate to its particular circumstances (the introduction section outlines a risk assessment process
ISO/IEC 17799 is expected to be renamed ISO/IEC 27002 in 2007. The ISO/IEC 27000 series has been reserved for information security matters with a handful of related standards such as ISO/IEC 27001 having already been released and others such as ISO/IEC 27004 – Information Security Management Metrics and Measurement – currently in draft.
We will examine Asset Management domain as an example of ISO17799.

ISO17799 in relation to ITIL
- ISO 17799 only addresses the selection and management of information security controls.
- It is not interested in underlying implementation details. For example:
- ISO 17799 is not interested that you have the latest and greatest logging and analysis products.
- ISO 17799 is not interested in HOW you log.
- Product selection is usually an operational efficiency issue (i.e. ITIL)
- ISO 17799 is interested in:
- WHAT you log (requirements).
- WHY you log what you do (risk mitigation).
- WHEN you log (tasks and schedules, window of vulnerability).
- WHO is assigned log analysis duty (roles and responsibilities).
- Satisfying these ISO 17799 interests produces defensible specifications and configurations that may ultimately influence product selection and deployment. (feeds into ITIL)

ISO17799 Example: Asset Management
- 7.1 Responsibility for assets:
- Objective:
- To achieve and maintain appropriate protection of organizational assets. All assets should be accounted for and have a nominated owner.
- Owners should be identified for all assets and the responsibility for the maintenance of appropriate controls should be assigned. The implementation of specific controls may be delegated by the owner as appropriate but the owner remains responsible for the proper protection of the assets.
- 7.2 Information Classification
- Implementation guidance is offered for all controls
Domain: Asset Management
7 Asset management
Control 7.1 Responsibility for assets
Control Objective: To achieve and maintain appropriate protection of organizational assets. All assets should be accounted for and have a nominated owner. Owners should be identified for all assets and the responsibility for the maintenance of appropriate controls should be assigned. The implementation of specific controls may be delegated by the owner as appropriate but the owner remains responsible for the proper protection of the assets.
7.1.1 Inventory of assets
Control
All assets should be clearly identified and an inventory of all important assets drawn up and maintained.
Implementation guidance
An organization should identify all assets and document the importance of these assets. The asset inventory should include all information necessary in order to recover from a disaster, including type of asset, format, location, backup information, license information, and a business value. The inventory should not duplicate other inventories unnecessarily, but it should be ensured that the content is aligned. In addition, ownership (see 7.1.2) and information classification (see 7.2) should be agreed and documented for each of the assets. Based on the importance of the asset, its business value and its security classification, levels of protection commensurate with the importance of the assets should be identified
Other information
There are many types of assets, including:
- information: databases and data files, contracts and agreements, system documentation, research information, user manuals, training material, operational or support procedures, business continuity plans, fallback arrangements, audit trails, and archived information;
- software assets: application software, system software, development tools, and utilities;
- physical assets: computer equipment, communications equipment, removable media, and other equipment;
- services: computing and communications services, general utilities, e.g. heating, lighting,power, and air-conditioning;
- people, and their qualifications, skills, and experience;
- intangibles, such as reputation and image of the organization.
Inventories of assets help to ensure that effective asset protection takes place, and may also be required for other business purposes, such as health and safety, insurance or financial (asset management) reasons. The process of compiling an inventory of assets is an important prerequisite of risk management
7.1.2 Ownership of assets
Control
All information and assets associated with information processing facilities should be owned2 by a designated part of the organization.
Implementation guidance
The asset owner should be responsible for:
- ensuring that information and assets associated with information processing facilities are appropriately classified;
- defining and periodically reviewing access restrictions and classifications, taking into account applicable access control policies.
Ownership may be allocated to:
- a business process;
- a defined set of activities;
- an application; or
- a defined set of data.
Other information
Routine tasks may be delegated, e.g. to a custodian looking after the asset on a daily bsis, but the responsibility remains with the owner.
In complex information systems it may be useful to designate groups of assets, which act together to provide a particular function as ‘services’. In this case the service owner is responsible for the delivery of the service, including the functioning of the assets, which provide it.
7.1.3 Acceptable use of assets
Control
Rules for the acceptable use of information and assets associated with information processing facilities should be identified, documented, and implemented.
Implementation guidance
All employees, contractors and third party users should follow rules for the acceptable use of information and assets associated with information processing facilities, including:
- rules for electronic mail and Internet usages (see 10.8);
- guidelines for the use of mobile devices, especially for the use outside the premises of the organization (see 11.7.1);
Specific rules or guidance should be provided by the relevant management. Employees, contractors and third party users using or having access to the organization’s assets should be aware of the limits existing for their use of organization’s information and assets associated with information processing facilities, and resources. They should be responsible for their use of any information processing resources, and of any such use carried out under their responsibility.
The term ‘owner’ identifies an individual or entity that has approved management responsibility for controlling the production, development, maintenance, use and security of the assets. The term ‘owner’ does not mean that the person actually has any property rights to the asset.

ISO17799 Example: Asset Management
- 7.1 Responsibility for assets:
- 7.2 Information Classification
- Objective:
- To ensure that information receives an appropriate level of protection.
- Information should be classified to indicate the need, priorities, and expected degree of protection when handling the information.
- Information has varying degrees of sensitivity and criticality. Some items may require an additional level of protection or special handling. An information classification scheme should be used to define an appropriate set of protection levels and communicate the need for special handling measures
- Implementation guidance is offered for all controls
7.2 Information classification
Objective: To ensure that information receives an appropriate level of protection.
Information should be classified to indicate the need, priorities, and expected degree of protection when handling the information.
Information has varying degrees of sensitivity and criticality. Some items may require an additional level of protection or special handling. An information classification scheme should be used to define an appropriate set of protection levels and communicate the need for special handling measures.
7.2.1 Classification guidelines
Control
Information should be classified in terms of its value, legal requirements, sensitivity, and criticality to the organization.
Implementation guidance
Classifications and associated protective controls for information should take account of business needs for sharing or restricting information and the business impacts associated with such needs. Classification guidelines should include conventions for initial classification and reclassification over time; in accordance with some predetermined access control policy (see 11.1.1). It should be the responsibility of the asset owner (see 7.1.2) to define the classification of an asset, periodically review it, and ensure it is kept up to date and at the appropriate level. The classification should take account of the aggregation effect mentioned in 10.7.2. Consideration should be given to the number of classification categories and the benefits to be gained from their use. Overly complex schemes may become cumbersome and uneconomic to use or prove impractical. Care should be taken in interpreting classification labels on documents from other organizations, which may have different definitions for the same or similarly named labels.
Other Information
The level of protection can be assessed by analyzing confidentiality, integrity and availability and any other requirements for the information considered.
Information often ceases to be sensitive or critical after a certain period of time, for example, when the information has been made public. These aspects should be taken into account, as over-classification can lead to the implementation of unnecessary controls resulting in additional expense.
Considering documents with similar security requirements together when assigning classification levels might help to simplify the classification task.
In general, the classification given to information is a shorthand way of determining how this information is to be handled and protected.
7.2.2 Information labeling and handling
Control
An appropriate set of procedures for information labeling and handling should be developed and implemented in accordance with the classification scheme adopted by the organization.
Implementation guidance
Procedures for information labeling need to cover information assets in physical and electronic formats.
Output from systems containing information that is classified as being sensitive or critical should carry an appropriate classification label (in the output). The labeling should reflect the classification according to the rules established in 7.2.1. Items for consideration include printed reports, screen displays, recorded media (e.g. tapes, disks, CDs), electronic messages, and file transfers. For each classification level, handling procedures including the secure processing, storage, transmission, declassification, and destruction should be defined. This should also include the procedures for chain of custody and logging of any security relevant event. Agreements with other organizations that include information sharing should include procedures to identify the classification of that information and to interpret the classification labels from other organizations.
Other Information
Labeling and secure handling of classified information is a key requirement for information sharing arrangements. Physical labels are a common form of labeling. However, some information assets, such as documents in electronic form, cannot be physically labeled and electronic means of labeling need to be used. For example, notification labeling may appear on the screen or display. Where labeling is not feasible, other means of designating the classification of information may be applied, e.g. via procedures or meta-data.

Benefits of Best Practices
- Avoiding re-inventing wheels
- Reducing dependency on technology experts
- Increasing the potential to utilize less-experienced staff if properly trained
- Making it easier to leverage external assistance
- Overcoming vertical silos and nonconforming behavior
- Reducing risks and errors
- Improving quality
- Improving the ability to manage and monitor
- Increasing standardization leading to cost reduction
- Improving trust and confidence from management and partners
- Creating respect from regulators and other external reviewers
- Safeguarding and proving value
- Helps strengthen supplier/customer relations, make contractual obligations easier to monitor and enforce

There are also some obvious, but pragmatic, rules that management ought to follow:
- Treat the implementation initiative as a project activity with a series of phases rather than a ‘one-off’ step.
- Remember that implementation involves cultural change as well as new processes. Therefore, a key success factor is the enablement and motivation of these changes.
- Make sure there is a clear understanding of the objectives.
- Manage expectations. In most enterprises, achieving successful oversight of IT takes time and is a continuous improvement process.
- Focus first on where it is easiest to make changes and deliver improvements and build from there one step at a time.
- Obtain top management buy-in and ownership. This needs to be based on the principles of best managing the IT investment.
- Avoid the initiative becoming perceived as a purely bureaucratic exercise.
- Avoid the unfocused checklist approach.

Free Information: Aligning CT , ITIL and ISO 17799 for Business Benefit: http://www.itgovernance.co.uk/files/Aligning%20ITIL,%20CobiT,%2017799.pdf
- IT best practices need to be aligned to business requirements and integrated with one another and with internal procedures.
- COBIT can be used at the highest level, providing an overall control framework based on an IT process model that should generically suit every organization.
- Specific practices and standards such as ITIL and ISO 17799 cover discrete areas and can be mapped to the COBIT framework, thus providing an hierarchy of guidance materials.
0 Comments on “IT Governance Standards: COBIT, ISO17799/27001, ITIL and PMBOK – Part 4”